3 tips for people who use Facebook but value their privacy
Thursday, April 22nd, 2010Volker Weber just blogged about thee things you can do to protect your privacy on facebook
1. Edit your Facebook Privacy Settings and uncheck "Instant Personalization"
2. Disable everything on this page to prevent others and applications from accessing and sharing your information
3. Volker also recommends blocking the following three applications: Microsoft Docs.com, Pandora and Yelp
Now, if I could just get rid of Farmville and Mafia wars forever.....
Source: Volker Weber
With 8.5.2, your Notes apps won’t look like Win95 anymore
Tuesday, April 20th, 2010I'm testing the beta version of Notes 8.5.2 and now that the ban on blogging has been lifted, I want to share one of the little things that Mary Beth Raven and her team have done that I think will make a BIG improvement in the perception of Notes in the marketplace. Support for 32-bit color icons has just been added to Notes 8.5.2!
Consider these two Notes applications and their icons:
The database icon on the left is the standard 16-bit color icon we all grew to know and love in the last century in the Windows for Workgroups 3.1 era. The database icon on the right is a PNG file that I selected as my DB Icon using the new 8.5.2 Designer client.
Continue Reading "With 8.5.2, your Notes apps won't look like Win95 anymore" »
Follow-up: How to stop sending Notes email to unintended recipients by disabling the recent contacts feature in Notes 8/8.5x
Friday, April 16th, 2010However, as you will see below, Notes sees the "RH" and arbitrarily decides that RH maps better to "Rhonda Small" who is NOT in my contact list but who is someone I once exchanged email with.
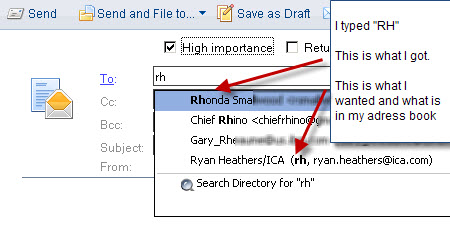
So, Rhonda gets the email intended for Ryan, Ryan does not get the email at all, and I'm left wondering whether I can trust my email system. Not pretty.
Thankfully, less than an hour after my post, am anonymous IBMer sent me a link to this document which provides more information on how the "recent contacts" feature works. It's a worthwhile read, although no end user should have to. What I learned from it and want to share with you is that it is insufficient to simply delete the recent -contacts as they will return and your problems may reappear in new ways as they did for me. IBM's tech note explains how to clear the recent contacts:
Continue Reading "Follow-up: How to stop sending Notes email to unintended recipients by disabling the recent contacts feature in Notes 8/8.5x" »
Caution! Notes 8/8.5x makes it easier than ever to send email to someone you didn’t intend to...
Thursday, April 15th, 2010I'm sharing a lesson I learned today in the hope that it might make you more productive and that I might learn something from the comments to this post. From a security/legal perspective, my hope is that this will save future embarrassment/liability as well.
It seems that I had unknowingly sent a private communication to an unintended public email address - in this case, an old mailing list for a KM community. Oops. This was not the first time it has happened to me so I decided to investigate.
I love the shortname feature in Notes because for as long as I can remember I simply type the initials of the person in my company address book and Notes routes the mail to the right person. I've worked this way in Notes for at least 15 years. Example: My wife's name is Kathy and her shortname is "KM". I type "KM" into the address field and the email gets to my wife. (We have similar shortnames for everyone on staff.) It sure beats looking up a name in a directory.
Since upgrading to Notes 8.5x I have noticed that more than once I have sent email to someone only to find that it went to someone else. Here's what I found.
Continue Reading "Caution! Notes 8/8.5x makes it easier than ever to send email to someone you didn't intend to..." »
GTD and Lotus Notes = Resounding Success
Tuesday, April 13th, 2010Guest post by Ryan Heathers
Last Thursday, we held an IBM employee-only "Getting Things Done in Lotus Notes" webinar with eProductivity's Eric Mack and featured guest, GTD® creator David Allen. Judging by the 725 IBMer registrants, the 200 questions asked during the session, and the multitudes of follow-up emails that attendees sent us, the webinar was a resounding success.
The webinar even generated the Tweet of the Month! (trademark pending, of course...)
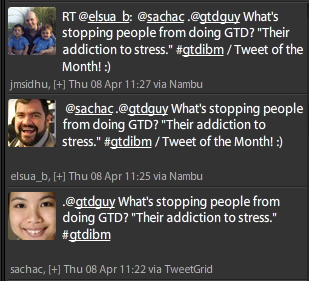
David and Eric were on fire and shared many things they've learned about being more productive with Lotus Notes.
 David delivered a passionate explanation of the Essentials of GTD. He spoke on the vital importance of a trusted system and reminded us that you can only feel good about what you're not doing if you know what you're not doing.
David delivered a passionate explanation of the Essentials of GTD. He spoke on the vital importance of a trusted system and reminded us that you can only feel good about what you're not doing if you know what you're not doing.
For those who had never heard of GTD, it was a eye-opening experience (based on their comments afterwards) and for those of us familiar with GTD, it was a welcome refresher.
Eric then showed how to set up Lotus Notes for GTD. First, he demonstrated how regular Lotus Notes can be an effective GTD list manager, and then he showed how using eProductivity takes Lotus Notes to the next level. The best part? It was all stuff people could put to use right away.
Plus, all attendees received a free resource kit which included an eProductivity Reference database full of great GTD articles from David's library.
First, let me say a big thanks to everyone who attended the webinar. Your participation was appreciated and it's been great to hear from so many of you about how the webinar benefited you.
Let me also say thanks to everyone who helped spread the word about the webinar.
Another opportunity to hear David and Eric live:
On April 28th, you have another opportunity to experience David and Eric's extensive knowledge of productivity.
This time, the free event is open to the general public but spaces are filling up quickly. So before the event is booked out, make sure to tell all your friends who use Lotus Notes and could use more time & less stress in their lives!
Register for the webinar
 Now, in case you're still deciding if this is the webinar for you, here's the planned agenda:
Now, in case you're still deciding if this is the webinar for you, here's the planned agenda:
Agenda
- Your Personal Productivity Equation
- Essentials of GTD
- How to set up Lotus Notes with GTD
- David's Productivity Toolkit
- eProductivity™ for IBM Lotus Notes
- Getting Started with GTD and Lotus Notes
- Q&A;
As you can see, this is a must-attend event! Register today.
To get automatic updates on eProductivity's webinar events, you can sign up for the free eProductivity newsletter.
When Social Software does an end-run around information security
Tuesday, April 13th, 2010No matter how secure our software may be, that security can be undermined, however, when Social Software applications outside the enterprise offer to "connect" you to your friends or people you may want to know.
What many people may not realize is that to do their "magic" and connect us with others, these social networking applications must scan your personal and company address books as well as your calendar and related information and upload it to a server where it can be indexed and cross referenced. That's the power of LinkedIn, Plaxo and similar "Social Networking" services and we are seeing more and more of these applications are showing up on the desktop, the web, and even in our mobile devices.
I consider myself a very security conscious individual and yet, today, I installed an application that forced me to reevaluate my own responsibilities toward the information on my system and what I choose to share externally. As soon as I installed the application, I noticed the CPU and network activity spike as I realized that my personal information in my encrypoted Notes databases was being scanned and that some of it was being sent outside my firewall to the service. Apparently, I had consented to this automatic upload when I installed the software, so shame on me. I had misunderstood the privacy agreement, which I did read. I thought that I would get to choose which information would be uploaded and when before the upload would happen. I was wrong. My bad. Fortunately, the company had a method in place to allow me to quickly delete my information from their service. It was a good wake-up call.
This does not mean that I will never use that software again. In fact, from a productivity and knowledge management perspective, I'm actually very intrigued by this class of software. I plan to do a more structured review of this and other similar applications in the near future because I think the productive potential is significant. At the same time, I am concerned that the relative ease of deploying Web 2.0 applications that so easily allow anyone to bypass the corporate firewall may create an environment where people do not consider, do not understand, or perhaps are simply unaware of the implications of what they are doing. Web 2.0 allows anyone to be their own IT manager; that's great but with that freedcom comes the need to take personal responsibility for the tools we use as well as how we use them.
Continue Reading "When Social Software does an end-run around information security" »
Speed up Lotus Notes with a Local Replica
Tuesday, April 6th, 2010Today, Darren Duke blogged about this and he provides the steps anyone can use to set up a local replica of a database.
How to break yourself (and others) of the email habit
Monday, April 5th, 2010Luis Suarez does just this as he shares three different principles he works at when whenever he processes his email, which he says he has down to about 10 minutes per day...
- Stop sending emails yourself
- Stop replying to emails
- Refuse to engage through email
Continue Reading "How to break yourself (and others) of the email habit" »